XSS in Bluestone Electron App when rendering mermaid class diagram Leading to RCE(Just Thanks)
Summary
Due to outdated mermaid 10.0.2 is used to render diagrams, a XSS in class diagram is able to trigger, chained with insecure configuration of windows electron app, attacker is able to execute code in victims’ local system.
Details
Bluestone is using mermaid 10.0.2 to render mermaid diagram. This issue have discussed the XSS in mermaid below 10.9.0 when rendering the node names of classDiagram. Specifically, The names of node are not fully sanitized which leads to injection of XSS payload.
Besides, the electron app sets nodeIntegration to true which is harmful, according to this attack, a XSS can be escalated to execute command on victims’ local system.
PoC
-
Download latest Bluestone v0.22.0 windows electron app from official repo, and install the application:
-
Open the payload markdown file using the Bluestone app, the payload is following:
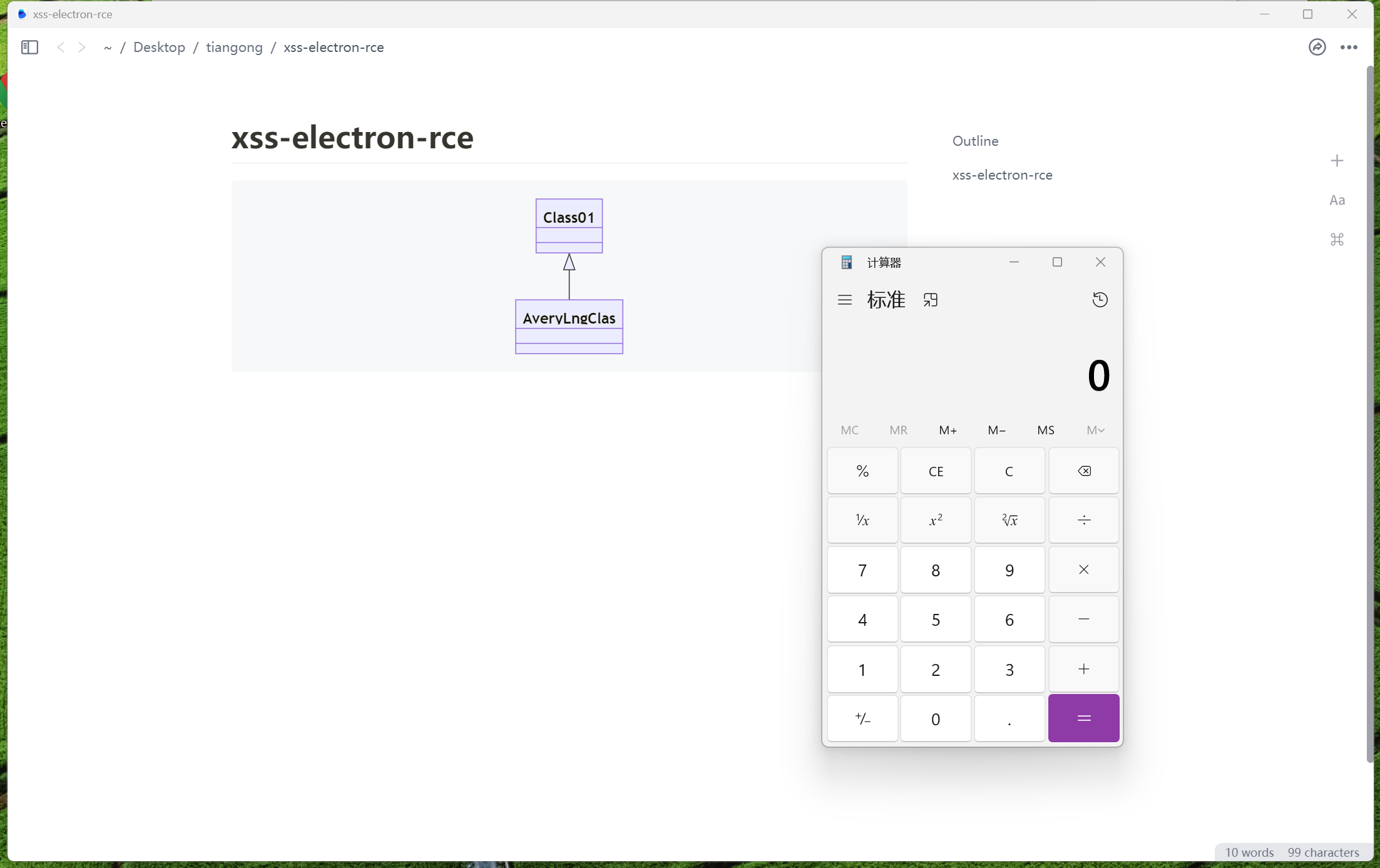
classDiagram Class01 <|-- `AveryLngClas<img src='x' onerror=require('child_process').exec('calc');>` -
The calculator poped up.
Impact
Client side code execution.
Reference
https://github.com/Milkdown/milkdown/issues/1267#issuecomment-2018032986
Occurence
https://github.com/1943time/bluestone/blob/07535f86adebe8f7f00c299ca60792189eff2a64/package.json#L67
Mitigation
- Upgrade the mermaid to latest version which is
10.9.1. - Disable
nodeIntegrationin electron app.